In a typical scenario, your landing page is available for anyone that has a link to it. This means that it can be viewed by someone who didn't go through your campaign URL and may have other intent than taking your offer.
Without right protection, it can get ripped at an insane speed and keep popping up on spy tools whenever you reach any volume.
How does it work?
1. You get a script that needs to be implemented on your landing page.
2. A special parameter called the lptoken that is automatically added to your lander URL.
Voluum then adds a unique value to this URL using this parameter and the script checks for that value.
Every visit that didn't go through Voluum and doesn't have the landing page token value will be blocked.
For every visit coming through a campaign URL, the landing page will be displayed and available for 30 minutes.
How to set it up?
I. Get the lander protection script
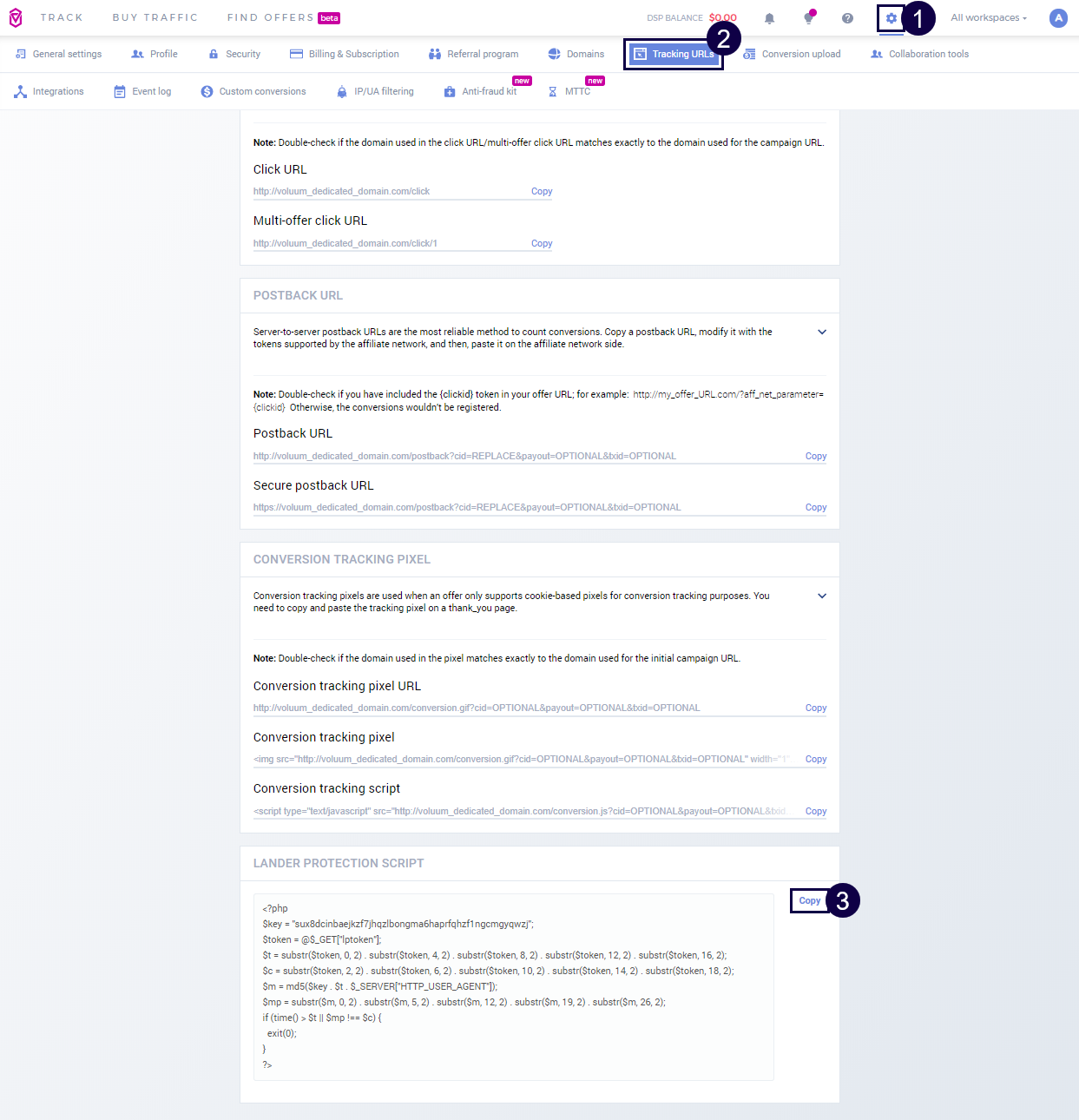
II. Paste the Lander Protection Script to your landing page
You’re good to go!
The lptoken is automatically added to all your lander URL, so you do not have to add it manually. Even it is not visible in a lander URL in Voluum, it will be visible after Voluum makes a redirect to the landing page. If you want to verify it, go through your campaign URL and check, if the lptoken is visible in the lander URL in your web browser's address bar. It should look like this: https://lander_url.com?lptoken=123456789
Without right protection, it can get ripped at an insane speed and keep popping up on spy tools whenever you reach any volume.
- Voluum has created a solution for you - let me introduce Lander Protection Script.
- It blocks access to your landing page from visitors or programs that didn't come through a campaign URL.
- What they will see instead is a blank page.
How does it work?
1. You get a script that needs to be implemented on your landing page.
2. A special parameter called the lptoken that is automatically added to your lander URL.
Voluum then adds a unique value to this URL using this parameter and the script checks for that value.
Every visit that didn't go through Voluum and doesn't have the landing page token value will be blocked.
For every visit coming through a campaign URL, the landing page will be displayed and available for 30 minutes.
How to set it up?
I. Get the lander protection script

II. Paste the Lander Protection Script to your landing page
You’re good to go!
The lptoken is automatically added to all your lander URL, so you do not have to add it manually. Even it is not visible in a lander URL in Voluum, it will be visible after Voluum makes a redirect to the landing page. If you want to verify it, go through your campaign URL and check, if the lptoken is visible in the lander URL in your web browser's address bar. It should look like this: https://lander_url.com?lptoken=123456789





