game333
Well-Known Member
Man, I was almost got my computer security hacked!
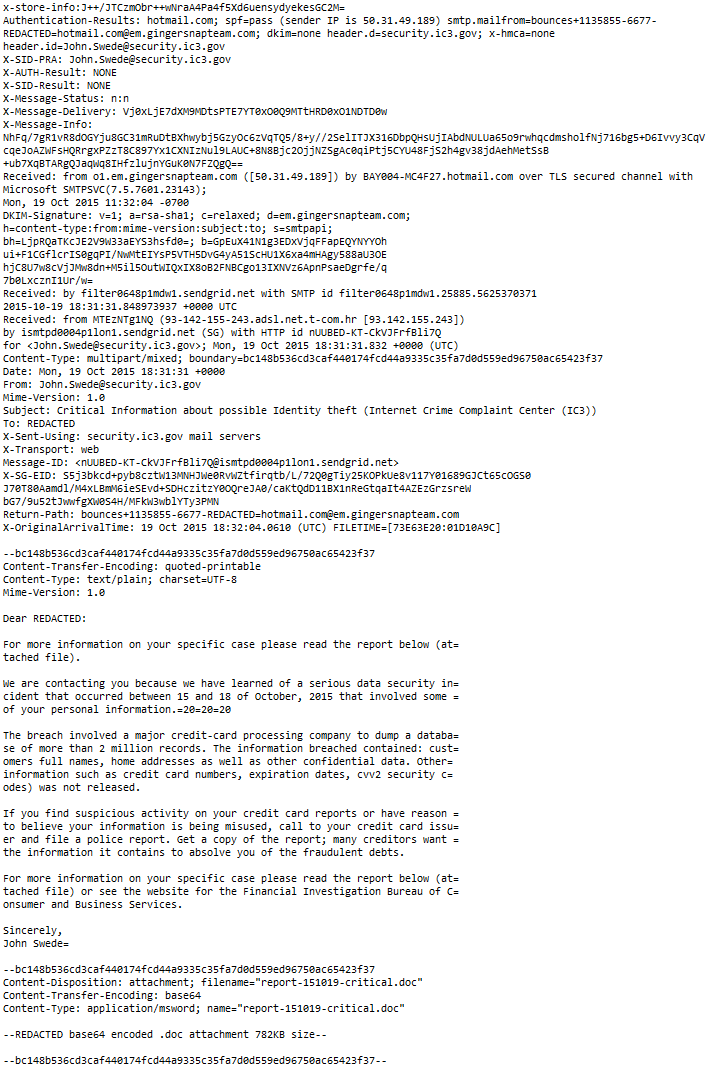
This email was sent from John.Swede@security.ic3.gov
security.ic3.gov
a .gov
That should be government domain!?
There's an attachment which formatted in .rtf
Hotmail couldn't open it and the description for the email is.
"Dear ...:
For more information on your specific case please read the report below (attached file).
We are contacting you because we have learned of a serious data security incident that occurred between 15 and 18 of October, 2015 that involved some of your personal information.
The breach involved a major credit-card processing company to dump a database of more than 2 million records. The information breached contained: customers full names, home addresses as well as other confidential data. Other information such as credit card numbers, expiration dates, cvv2 security codes) was not released.
If you find suspicious activity on your credit card reports or have reason to believe your information is being misused, call to your credit card issuer and file a police report. Get a copy of the report; many creditors want the information it contains to absolve you of the fraudulent debts.
For more information on your specific case please read the report below (attached file) or see the website for the Financial Investigation Bureau of Consumer and Business Services.
Sincerely,
John Swede"
I then zip the .rtf do a scanning on virustotal, shocking...
Antivirus scan for a53787b4f0390f349690f9b5a6a1644234eba00aa8168e7869efed51577d7fb2 at 2015-10-19 18:24:11 UTC - VirusTotal
If 1 out of 50 scanned as a malware, then it will be an false alarm but 4/56
Very dangerous, be alert if you receive an email with attachment, never open it, zip it, don't execute.
This email was sent from John.Swede@security.ic3.gov
security.ic3.gov
a .gov
That should be government domain!?
There's an attachment which formatted in .rtf
Hotmail couldn't open it and the description for the email is.
"Dear ...:
For more information on your specific case please read the report below (attached file).
We are contacting you because we have learned of a serious data security incident that occurred between 15 and 18 of October, 2015 that involved some of your personal information.
The breach involved a major credit-card processing company to dump a database of more than 2 million records. The information breached contained: customers full names, home addresses as well as other confidential data. Other information such as credit card numbers, expiration dates, cvv2 security codes) was not released.
If you find suspicious activity on your credit card reports or have reason to believe your information is being misused, call to your credit card issuer and file a police report. Get a copy of the report; many creditors want the information it contains to absolve you of the fraudulent debts.
For more information on your specific case please read the report below (attached file) or see the website for the Financial Investigation Bureau of Consumer and Business Services.
Sincerely,
John Swede"
I then zip the .rtf do a scanning on virustotal, shocking...
Antivirus scan for a53787b4f0390f349690f9b5a6a1644234eba00aa8168e7869efed51577d7fb2 at 2015-10-19 18:24:11 UTC - VirusTotal
If 1 out of 50 scanned as a malware, then it will be an false alarm but 4/56
Very dangerous, be alert if you receive an email with attachment, never open it, zip it, don't execute.