The Trillium Security Multisploit Tool V4 Private Edition is an advanced penetration testing and ethical hacking framework designed for security professionals, red teams, and cybersecurity researchers. This tool integrates multiple exploitation techniques, vulnerability scanners, and post-exploitation modules into a single unified platform.
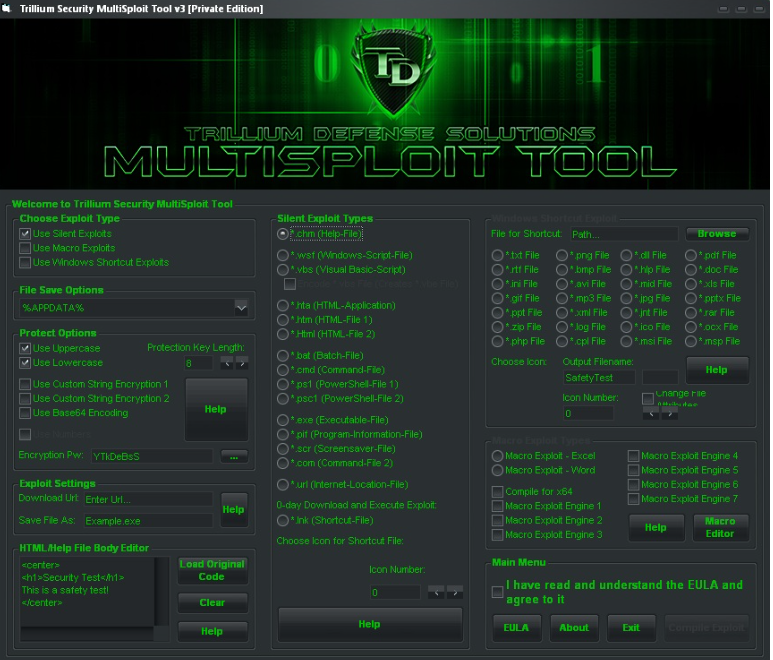

Key Features of Trillium Security Multisploit Tool V4 Private Edition
1. Multi-Vector Exploitation Framework
- Supports exploits for Windows, Linux, Android, and IoT devices.
- Includes zero-day exploits (privately disclosed) for advanced penetration testing.
- Modular architecture for easy integration of new exploits.
2. Automated Vulnerability Scanning
- Network Scanning: Detects open ports, services, and misconfigurations (using techniques similar to Nmap).
- Web Application Testing: SQLi, XSS, CSRF, and API vulnerability detection.
- Wireless Security Auditing: WPA2/WPA3 cracking, rogue AP detection, and MITM attack simulations.
3. Post-Exploitation Modules
- Privilege Escalation: Local exploits for Windows (DLL hijacking, token impersonation) and Linux (SUID, kernel exploits).
- Persistence Mechanisms: Backdooring, scheduled tasks, and registry modifications.
- Data Exfiltration: Stealthy extraction of sensitive files, credentials, and logs.
4. Custom Payload Generation
- Polymorphic malware evasion (bypassing AV/EDR).
- Encrypted C2 (Command & Control) channels for secure remote access.
- Support for Meterpreter, Shellcode, and Custom Binaries.
5. Stealth & Anti-Forensics
- Memory-only execution (fileless attacks).
- Log manipulation & clearing traces (event logs, bash history).
- Rootkit capabilities (for advanced red team operations).
6. Reporting & Analytics
- Automated PDF/HTML reports with CVSS scoring.
- Vulnerability prioritization (critical, high, medium, low).
- Integration with SIEM tools (Splunk, ELK Stack).